Uses of Digital Certificates
Digital certificate adopts the Public Key Infrastructure (PKI) framework for enabling the deployment of its three major functional uses – Public Key Encryption, Digital Signature and Electronic Authentication.
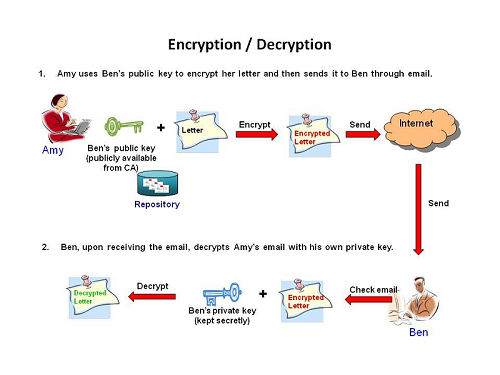
Public Key Encryption is a means to ensure confidentiality of message. It involves encryption of data with a pair of asymmetric but matching keys – a private key and a public key. Private key is kept secretly and securely by the owner of the digital certificate and the corresponding public key is published at an online repository by certification authority (CA) and publicly available for others to use. Encryption is performed by encoding data using the public key of the certificate holder and decryption is only possible by decoding the encrypted data using the corresponding private key of the holder.
Taking email message transmission as an example, the privacy of messages sent via email can be protected by encryption with a recipient's public key. Since no other means / key except the recipient's private key can decrypt the encrypted message, the confidentiality of the email content can be secured.
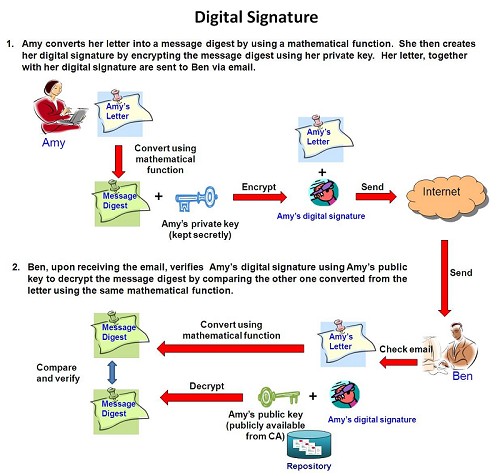
Digital Signature created by means of digital certificate can serve to ensure data integrity, user authenticity and non-repudiation of transaction. A digital signature is derived by applying a mathematical function to compute a message digest of an electronic message (say, a letter), and then encrypt the digest with the sender's private key. The electronic message together with the digital signature will be sent to the recipient(s). Recipient(s) can verify the sender's digital signature with the use of the sender's public key.
Taking signing an email as an example, if a digitally signed email has not been tampered with during the course of transmission (data integrity), the digital signature will be verified correctly by the recipient using the sender's public key. Since the sender is the only person who has the access to his/her own private key and once the digital signature is verified as valid using the sender's public key, the recipient can be certain that the email is indeed come from the sender (user authenticity) and the sender cannot deny having created and signed the email (non-repudiation of transaction).
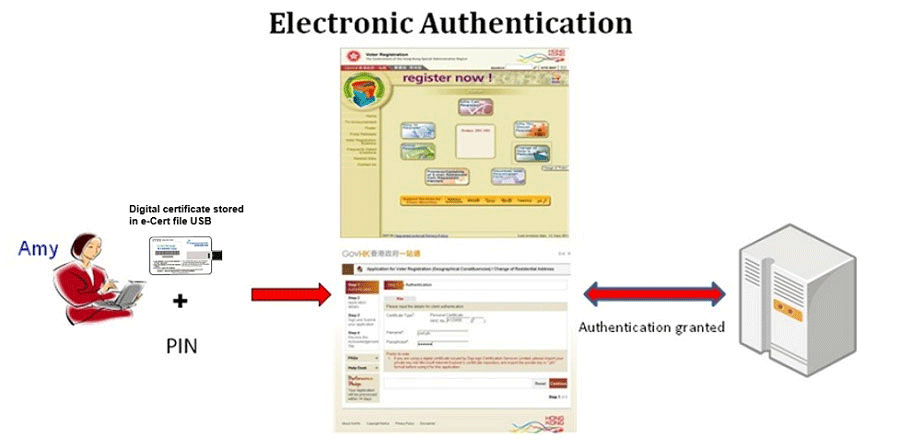
Electronic Authentication is the process of confirming user identity presented electronically to an information system for accessing data or conducting transactions. Digital certificate, among others, is one of the effective authentication factors that can achieve high degree of confidence in asserting user identity in the registration and authentication processes.
To illustrate how to make an electronic authentication, Amy uses her digital certificate stored in the e-Cert file USB as one of the authentication factors, together with her personal identification number (PIN), to authenticate herself to an online transaction, say to change her personal particulars under voter registration in GovHK. The application verifies her identity via the digital certificate and allows her to change her particulars.
More on securing access using e-Authentication is available at the InfoSec website.
Public Key Infrastructure provides a safe and reliable environment for electronic transactions in the Internet. It is a security framework involving technical mechanisms, policies and procedures that adopts public key encryption technique to protect the confidentiality, integrity, authenticity and non-repudiation of data.